AWS CLI for Security Investigations
Last Updated :
18 Sep, 2024
The AWS Command Line Interface (AWS CLI) is a powerful tool that provides a uniform method for managing your AWS resources. It acts as a connecting point for interacting with various AWS services, allowing users to perform tasks quickly and efficiently from the command line. With the AWS CLI, you have a single, comprehensive tool that simplifies the management of your cloud infrastructure.
With the AWS CLI, you only need to download and configure one tool to control and automate multiple AWS services. Whether you want to deploy applications, manage resources, or gather information, the AWS CLI allows you to run commands and scripts effortlessly. This not only saves you time but also minimizes the chance of errors, letting you focus on building and maintaining your cloud applications.
What is AWS CLI?
The AWS CLI is a command-line tool for AWS services. After installing and configuring the AWS CLI program with your AWS, you may operate AWS services from the command line and automate tasks using scripts. Because it supports scripting into a range of development and operational settings, it is an adaptable option for AWS Users.
Prerequisites of AWS CLI for Security Investigations
- AWS Account: All security-related services, including CloudTrail, GuardDuty, and IAM, require an active AWS account with permissions.
- AWS CLI Installed: After that you need to check the computer will have the AWS Command Line Interface, or CLI
- AWS CLI Configured: Configure AWS CLI with your credentials and default region after installation.
- IAM permission: Ensure the role or AWS user you are logging in with has the necessary permissions to view security events. The most common services utilized when storing evidence in a security investigation.
Step-by-Step Guide to AWS CLI for Security Investigations
Here is the step-by-step implementation of AWS CLI for Security Investigations:
Step 1: Enable AWS CloudTrail and Query Logs
To get started, CloudTrail logs every AWS API call. Use it to discover specifics about what users or services have done.
aws cloudtrail create-trail --name my-trail --s3-bucket-name my-bucket
aws cloudtrail start-logging --name my-trail
Output:

Step 2: Monitor IAM Activity
Confirming that unknown activities are present, like permissions or unauthorized access changes- View the last user actions performed and the user roles.
aws iam list-users
Output:

Step 3: Monitor S3 Bucket Activity
Next, Unauthorized S3 access may indicate a security breach.
aws s3 ls
Output:

Step 4: Investigate Security Groups
It is, therefore important, that you have a review of your settings in your security group before you access the VPC flow log to detect any unusual configuration of the network or rules set up to be too lenient.
aws ec2 describe-security-groups
Output:

Step 5: Query VPC Flow Logs
VPC Flow Logs keep track of all IP traffic entering and leaving your VPC's network interfaces.
aws ec2 describe-flow-logs
Output:

Step 6: Check GuardDuty Findings
In the next step, GuardDuty analyzes DNS logs, VPC Flow Logs, and AWS CloudTrail to assist find any security risks.
aws guardduty create-detector --enable
Output:

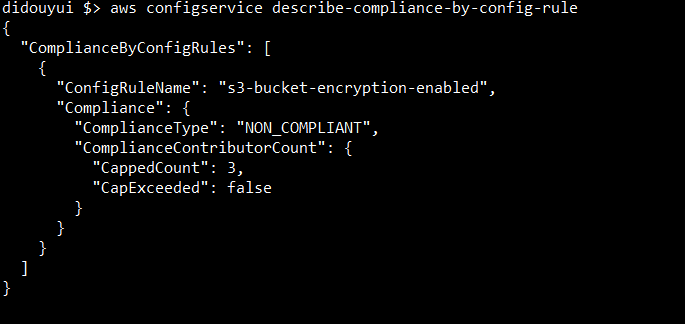
Step 7: Review AWS Config for Policy Violations
Finally, AWS Config keeps track of changes made to AWS useful things/valuable supply setups. It helps in locating useful things/valuable supplies that are not cooperative.
aws configservice describe-compliance-by-config-rule
Output:
Best Practices of AWS CLI for Security Investigations
- Use Amazon GuardDuty: Amazon GuardDuty is a threat detection service that protects your accounts, containers, workloads, and data in your AWS (surrounding conditions).
- Automate and Centralize Security Monitoring: Manual research can make mistakes. Centralized monitoring helps find security issues
- Enable CloudTrail's log file integrity: Validated log files are very useful for security and forensic investigations. For example, a validated log file allows you to confidently state that the log file has not changed or that specific IAM identity credentials conducted a specific API activity.
- Use the AWS Security Hub: Using AWS Security Hub, you may monitor how you use CloudTrail about security best practices. Security Hub employs detective security controls to examine useful things/valuable supply setups and security needed things, helping you in obeying multiple.
Conclusion
In conclusion, the AWS Command Line Interface (AWS CLI) runs the start-investigation command using this. Detective connects with Amazon Security Lake, which allows you to query and obtain raw log data stored in Security Lake.
Similar Reads
AWS CLI for Service Health Monitoring
AWS has numerous services, and for your application to run smoothly, it is necessary to keep a check on the status of the services. AWS CLI provides a unified set of commands that enable you to programmatically monitor the health and status of AWS services and resources. Monitoring service health th
6 min read
AWS CLI for Relational Database Service
As we know, Amazon Web Services (AWS) provides more than 200 IT and infrastructure management services. The question arises: can we only access and manage those services through the AWS Management Console? The answer is no. We can access and interact with those services through the AWS Management Co
7 min read
AWS CLI for Continuous Integration
Quick and efficient delivery of quality code is at the core of software development in the fast-paced arena. Practically, Continuous Integration (CI) has emerged as a lynchpin practice to this aim, where developers regularly integrate changes in the code into the shared repository. These integration
6 min read
AWS CLI for Conversational Interfaces
Chatbots and voice assistants have now made it easy for users to have conversations with applications, AWS has services—Amazon Lex and Amazon Polly, to name a few—that make the development of intelligent applications easier. But the AWS CLI makes it easy to manage these services programmatically. AW
7 min read
How to Install AWS CLI on Ubuntu?
The AWS Command Line Interface (CLI) is a unified tool to manage your AWS services. With just one tool to download and configure, you can control multiple AWS services from the command line and automate them through scripts. Here are the step-by-step instructions to install AWS CLI on UbuntuStep 1:
3 min read
Cyber Crime Investigation
Cybercrime investigation is important because activities such as hacking, fraud, and identity theft may result in very dangerous consequences for individuals, businesses, and national security. Effective investigation helps recognize and avoid cybercriminals to save digital properties and sustain on
8 min read
Step Functions Mastery: AWS CLI for Serverless Orchestration
In the cloud computing, serverless architecture has restructured how developers build and deploy an applications. AWS Step Functions is a important service that orchestrates multiple AWS services into serverless workflows, allowing hard business processes to be automated with ease. What is AWS CLI ?
5 min read
AWS CLI for Serverless Function Management
Serverless computing is changing everything about how we build and deliver applications. No need for the onerous task of managing servers—developers can focus all their attention entirely on writing code and implementing functionalities. Among today's top serverless platforms, AWS Lambda supports ru
6 min read
What is Security Automation?
Security automation is revolutionizing the field of cybersecurity, providing businesses with advanced tools to enhance their defenses against cyber threats. Security automation uses technology to automate cybersecurity which speeds up threat detection, incident response, and vulnerability management
8 min read
Jenkins - Security Best Practices
Pre-requisite: Jenkins Jenkins is an open-source automation server that offers hundreds of plugins to help you build, deploy, and automate your projects. It is commonly used in continuous integration and continuous delivery (CI/CD) to automate the software delivery process. Jenkins runs on various p
11 min read