In today’s cyber threat landscape, attackers no longer rely on a single piece of malware to compromise networks — they use a coordinated chain of specialized tools. One of the most infamous examples of this collaboration is the Emotet > TrickBot > Ryuk attack sequence, also known as the Phish-to-Ransomware Chain.
This sophisticated campaign begins with a phishing email that drops Emotet, which then delivers TrickBot to steal credentials and map the network. Finally, the attackers deploy Ryuk ransomware to encrypt systems and demand massive ransom payments. Together, these three malware families form a multi-stage, modular attack ecosystem capable of turning a single email click into a full-scale organizational breach within hours.
Background Context
Between 2018 and 2021, many public and private sector organizations (especially in healthcare, finance, education, and manufacturing) experienced coordinated ransomware incidents involving the following sequence:
- Emotet acted as the initial loader, entering systems via phishing.
- TrickBot was used for credential theft, reconnaissance, and network propagation.
- Ryuk ransomware was the final payload used to encrypt and extort.
This “malware supply chain” was operated by cybercriminal partnerships rather than a single threat group, demonstrating the rise of malware-as-a-service (MaaS) models.
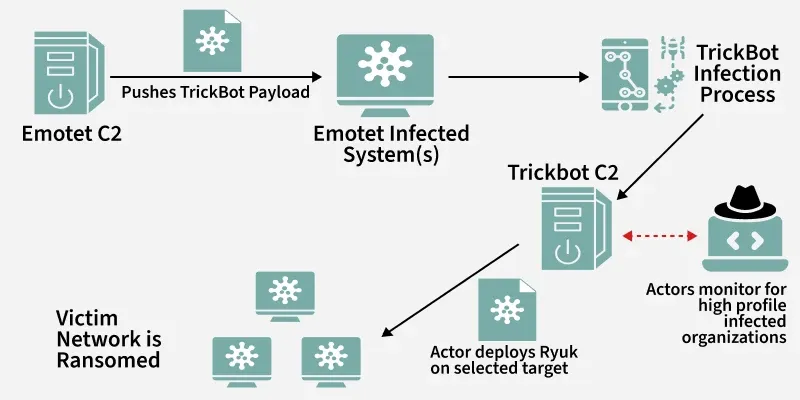
1. Initial Compromise: Emotet
The attack originated when an employee at a financial organization received a phishing email disguised as a legitimate invoice from a trusted vendor. The email included a malicious Microsoft Word attachment that urged the recipient to “Enable Content” to view the document. Once macros were enabled, the embedded Emotet payload was executed, silently installing the malware onto the system and establishing a foothold in the network.
- Objective: Establish initial access and persistence.
- Activity: Emotet downloaded additional payloads and communicated with its Command & Control (C2) servers over HTTPS.
- Result: The attacker gained a foothold within the victim network.
2. Secondary Infection: TrickBot
After the initial compromise, Emotet downloaded and executed TrickBot, a modular malware designed for credential harvesting and network reconnaissance.
- Objective: To expand access within the network and prepare for lateral movement.
- Activity: TrickBot extracted credentials from web browsers, Windows accounts, and Active Directory, while conducting SMB enumeration to map shared drives and identify high-value targets.
- Result: The attackers successfully escalated privileges, ultimately gaining domain-level control across the organization’s network.
3. Final Payload: Ryuk Ransomware
Once TrickBot completed its reconnaissance and credential theft, the attackers deployed Ryuk ransomware across the compromised network.
- Objective: To encrypt critical systems and extort the organization for financial gain.
- Activity: Ryuk used AES-256 encryption to lock essential servers, databases, and even backup repositories, appending the “.RYUK” extension to all encrypted files.
- Result: The attack caused a complete operational shutdown, with a ransom note demanding millions in Bitcoin for decryption keys and data restoration.
Mitigation Strategies for the Emotet > TrickBot > Ryuk Attack Chain
There are several layers of mitigation strategies to defend against the Emotet > TrickBot > Ryuk attack chain:

1. Email Security and Phishing Defense
- Implement advanced email filters to detect and quarantine phishing emails with malicious attachments or links.
- Use sandboxing solutions to analyze attachments (like Word or Excel files) before delivery.
- Conduct regular phishing awareness training to teach employees to identify and report suspicious emails.
2. Macro and Script Control
- Disable macros by default in Microsoft Office applications, especially for files downloaded from the internet.
- Use Group Policy to restrict script execution (PowerShell, VBScript) unless digitally signed.
- Employ Application Whitelisting (AppLocker or WDAC) to allow only approved applications to run.
3. Network Segmentation and Lateral Movement Prevention
- Segment networks to limit access between departments or systems.
- Use least privilege principles and multi-factor authentication (MFA) for administrative accounts.
- Monitor SMB and RDP traffic for unusual connections, as TrickBot often uses these for propagation.
- Deploy Endpoint Detection and Response (EDR) solutions to detect abnormal privilege escalation.
4. Credential Protection
- Enforce strong password policies and rotate admin credentials regularly.
- Store sensitive credentials in secure vaults (e.g., CyberArk, HashiCorp Vault).
- Use LSASS protection to prevent credential dumping by tools like Mimikatz (used by TrickBot modules).
5. Backup and Recovery Planning
- Maintain offline, immutable backups that cannot be accessed or encrypted by malware.
- Regularly test backup restoration to ensure business continuity.
- Implement versioning in cloud storage to recover previous unencrypted copies.
6. Threat Intelligence and Continuous Monitoring
- Subscribe to threat intelligence feeds to stay updated on IoCs related to Emotet, TrickBot, and Ryuk.
- Use SIEM tools (like Splunk or ELK) for centralized log monitoring and correlation.
- Regularly hunt for known IoCs such as Emotet email indicators, TrickBot C2 domains, or Ryuk file signatures.
7. Patch and Update Management
- Ensure all systems, including Windows, Office, and browsers, are regularly patched.
- Update antivirus and EDR signatures frequently to detect evolving variants.
- Use automated vulnerability scanners to identify and remediate outdated software.
8. Incident Response Preparedness
- Develop a well-defined incident response (IR) plan that includes containment, eradication, and recovery steps.
- Conduct tabletop exercises to simulate ransomware incidents and train teams for quick response.
- Ensure law enforcement and CERT contacts are predefined for immediate reporting.
Explore
Introduction to Ethical Hacking
Foot Printing and Reconnaissance
Scanning Networks
Enumeration
System Hacking
Malware Analysis
Sniffing
Social Engineering
Denial-of-Service
Session Hijacking