QakBot, also known as QBot or Pinkslipbot, is a sophisticated banking Trojan that evolved into a modular malware platform used for credential theft, lateral movement, and ransomware deployment. Initially designed to steal financial information, QakBot has become a central component in large-scale cybercrime operations, often acting as a gateway for ransomware infections such as Conti or ProLock.
Background and Evolution
First detected in 2007, QakBot primarily targeted online banking users. Over the years, it evolved from a standalone Trojan into a versatile malware platform, maintained and distributed by organized cybercriminal groups.
Its evolution includes:
- Expanding from credential theft to network infiltration and persistence
- Integration with other malware families, such as Emotet and TrickBot
- Acting as a loader for major ransomware operations, including Conti, REvil, and Black Basta
By 2021, QakBot had become a central figure in malware-as-a-service (MaaS) ecosystems, serving as the entry point for large-scale enterprise breaches.
Operational Workflow of QakBot
QakBot (QBot) is a modular banking Trojan turned general-purpose malware platform. Its operational workflow is a multi-stage chain that turns a single successful phishing click into full domain compromise and often ransomware deployment. Below is a concise, step-by-step explanation of how QakBot typically operates, what it does at each stage, and what to watch for.
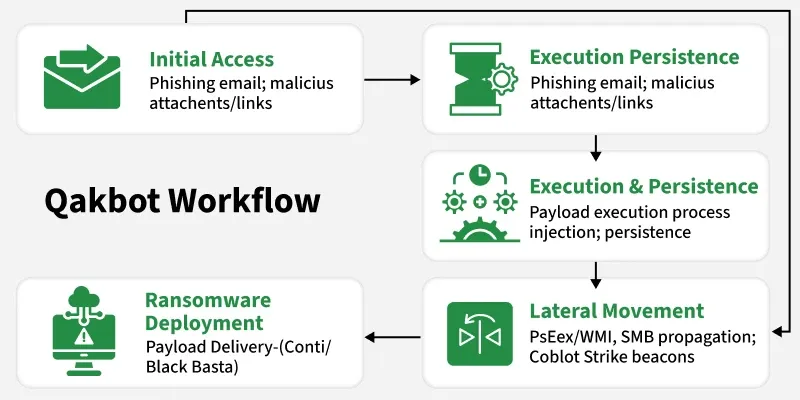
Step 1: Initial Access — Business Email Compromise (BEC)
QakBot campaigns typically start with phishing emails sent from compromised business accounts or spoofed domains. These emails appear legitimate — referencing invoices, HR notices, or internal reports — and contain either:
- Malicious attachments (Excel or Word documents with embedded macros), or
- Links to fake cloud storage pages hosting the malware.
Once the user opens the attachment and enables macros, a PowerShell or VBScript executes, silently downloading and running the QakBot payload.
Step 2: Execution and Persistence
After installation, QakBot embeds itself within system directories and injects code into trusted processes (like explorer.exe or wermgr.exe) to remain hidden. Persistence mechanisms include:
- Registry key modifications
- Scheduled tasks
- Startup folder entries
- This ensures the malware survives reboots and user logins undetected.
Step 3: Credential Theft and Reconnaissance
Once established, QakBot collects valuable data:
- Browser-stored credentials and cookies
- Email accounts, contact lists, and conversation histories
- Windows credentials harvested using Mimikatz-like modules
It performs network reconnaissance via LDAP queries and SMB enumeration, mapping domain structures and identifying administrative targets for further exploitation.
Step 4: Lateral Movement
With valid credentials in hand, QakBot moves laterally across the network using legitimate administrative tools.
Common techniques include:
- PsExec and WMI commands for remote execution
- SMB-based propagation to accessible hosts
- Deploying Cobalt Strike beacons for remote control and pivoting
This lateral spread allows attackers to escalate privileges, disable defenses, and prepare for the final stage of attack.
Step 5: Payload Delivery — Ransomware Deployment
QakBot often serves as a precursor to ransomware attacks. Once attackers have full network visibility and control, they deploy ransomware such as Conti or Black Basta, encrypting systems and exfiltrating sensitive data.
Victims are then subjected to double extortion — forced to pay to both decrypt data and prevent public data leaks.
Technical Components
1. Command & Control (C2)
C2 (Command & Control) is the communication channel between the attacker and infected systems (bots).
Key Points:
1. Encrypted HTTPS Communication:
- Modern malware uses HTTPS (port 443) to hide traffic within legitimate encrypted web traffic, making detection harder.
2. Peer-to-Peer (P2P) Fallback:
- If main C2 servers are blocked, infected machines can share commands among themselves using P2P communication, ensuring persistence.
3. Domain Generation Algorithms (DGAs):
- Malware generates random domain names daily to connect to new C2 servers dynamically, avoiding static detection.
4. Beaconing Behavior:
- The malware periodically “beacons” (pings) the C2 for updates, exfiltrates data, or receives new commands.
5. Redundancy & Resilience:
- Multiple C2 channels (HTTP, DNS tunneling, Tor) are often built in so that if one is disrupted, others continue the operation.
2. Modules
Malware uses modular architecture, meaning it loads additional components for specific malicious functions.
Key Points:
1. Credential Theft Module:
- Extracts credentials from browsers, memory (e.g., LSASS process), or password vaults like Windows Credential Manager.
2. Email Harvesting Module:
- Scans Outlook, Thunderbird, or stored PST files to gather contact lists for further phishing campaigns.
3. Proxy Tunneling Module:
- Converts infected hosts into proxy servers to hide attacker traffic and enable lateral movement.
4. Modular Design Flexibility:
- Attackers can update or deploy new modules without reinstalling the malware, making it adaptive.
5. Persistence Modules:
- Some modules ensure the malware reactivates after reboot (via scheduled tasks, registry keys, or services).
3. Anti-Analysis Techniques
These are defensive mechanisms inside malware designed to evade detection or hinder analysts.
Key Points:
1. Virtual Machine (VM) Detection:
- Malware checks system artifacts (e.g., VMware drivers, sandbox file names) and stops running if a sandbox is detected.
2. Execution Delay (Time Bombs):
- Introduces artificial delays (e.g., 5–10 minutes) before activating, tricking analysts who observe short execution windows.
3. Encrypted Internal Configuration:
- Stores its config (C2 URLs, encryption keys, campaign IDs) in encrypted form to prevent easy reverse engineering.
4. Code Obfuscation and Packing:
- Uses packers or encryption layers to hide actual malicious code from static analysis tools.
5. Anti-Debugging Tricks:
- Detects debugging tools (like OllyDbg or x64dbg) or manipulates API calls to crash debuggers during inspection.
Real-World Example — QakBot Attack on a Financial Services Firm (2021)
1️. Initial Compromise: Phishing Entry Point
- The attack began with a phishing email that appeared to come from the company’s HR department, referencing an “Updated Employee Policy” or “Benefits Review.”
- The email contained an Excel attachment with malicious macros.
- When an employee opened it and enabled macros, it silently downloaded and executed the QakBot payload.
- Why it worked: The email looked authentic, came from a trusted internal-looking domain, and used social engineering (HR-related topics) to lower suspicion.
2. Payload Execution — QakBot Activation
- Once executed, QakBot injected itself into legitimate system processes like
explorer.exe to stay hidden. - It established persistence by modifying registry keys and creating scheduled tasks, ensuring it survived reboots.
- Impact: The malware gained a permanent foothold in the corporate network, undetected by standard antivirus tools.
3. Privilege Escalation — Domain Administrator Compromise
- QakBot quickly began harvesting credentials using built-in modules and tools like Mimikatz.
- With stolen credentials, attackers escalated privileges to gain Domain Administrator access, giving them full control over the network.
- Impact: Attackers could now disable defenses, deploy payloads, and manage systems remotely.
4️. Lateral Movement — Cobalt Strike Deployment
- Attackers then deployed Cobalt Strike beacons, which allowed remote control of multiple systems.
- Through PsExec, SMB, and WMI, they moved laterally to critical servers and data centers.
- Purpose: To spread QakBot and prepare for a coordinated ransomware attack.
5️. Final Stage — Ransomware (Conti) Execution
- Once the attackers had full network visibility, they launched Conti ransomware, encrypting business-critical files and databases.
- A ransom note appeared, demanding multi-million-dollar payments in cryptocurrency to decrypt data and avoid public leaks.
Impact:
- Major operational downtime (banking services halted).
- Client data exposure (some customer records leaked).
- Months-long recovery process involving forensic investigation and infrastructure rebuild.
Explore
Introduction to Ethical Hacking
Foot Printing and Reconnaissance
Scanning Networks
Enumeration
System Hacking
Malware Analysis
Sniffing
Social Engineering
Denial-of-Service
Session Hijacking