A Zero Trust Architecture (ZTA) is a cybersecurity architecture that is based on zero trust principles and designed to prevent data breaches and limit internal lateral movement. The zero trust principles are based on the idea: "Never Trust, Always Verify." It includes various security technologies, such as:
- Identity and Access Management (IAM)
- Multi-factor Authentication (MFA)
- Micro-segmentation
- Encryption
- Real-time Monitoring
Zero Trust Architecture outlines how these principles are applied across an enterprise's systems, networks, and workflows to ensure that no entity (user, device, or application) gains access without thorough validation.
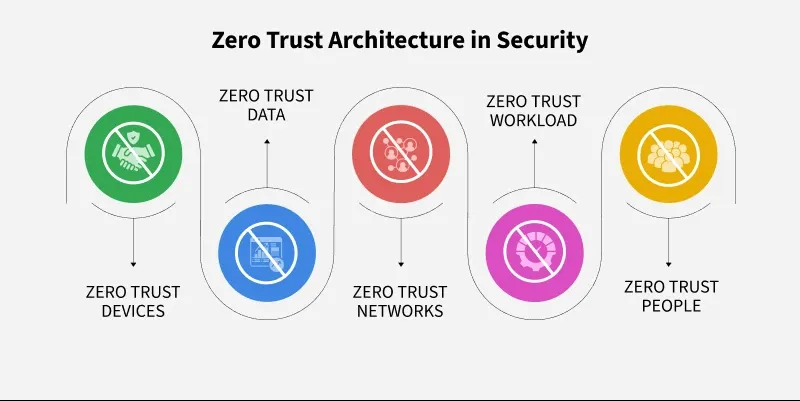
Zero Trust Basics
Zero trust is a cybersecurity model which is focused on resource protection and belief that trust is never granted implicitly but must be constantly evaluated. Zero Trust Architecture is a security concept that redefines how we protect systems, data, and users. It is an end-to-end approach to enterprise resource and data security that contains identity (person and non-person entities), credentials, access management, operations, endpoints, hosting environments, and the interconnecting infrastructure.
Zero trust (ZT) provides a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised.
Principles of Zero Trust Architecture
These are the 3 core principles, based on NIST 800-207, define how Zero Trust is implemented to ensure continuous, context-aware security enforcement.
1. Verify Explicitly
According to the core tenets described in the Zero Trust model based on NIST 800-207, verification must be applied continuously and dynamically to ensure that access is granted based on real-time risk assessments. This includes risk-based conditional access, rapid and scalable policy deployment, and comprehensive identity verification.
As per NIST:
- Authentication and authorization (both subject and device) are discrete functions performed before a session to an enterprise resource is established.
- Verification involves evaluating device posture, user identity, time, location, and other context before granting access.
2. Use Least Privilege Access
Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA), risk-based adaptive policies, and data protection.
- The principle of least privilege restricts users’ access rights to only the data, applications, and services they need to perform their authorized functions.
- Enforced through granular access controls, Just-in-Time (JIT) and Just-Enough Access (JEA) mechanisms.
- Identity-based segmentation provides a more flexible and effective way to control access, directly tied to the identity of the user or device.
As per NIST 800-207:
- Access rules are made as granular as possible to enforce least privileges needed to perform the action in the request.
- Authentication and authorization to one resource will not automatically grant access to a different resource.
3. Assume Breach
Zero Trust assumes that security breaches are unavoidable and the threats that cause them can be inside and outside an organization’s network perimeter. A key objective of Zero Trust architecture is to minimize the blast radius of a breach when it occurs.
Assets should always act as if an attacker is present on the enterprise network, and communication should be done in the most secure manner available this includes:
- Micro-segmentation of sensitive resources
- End-to-end encryption
- Continuous monitoring of user and device behavior for anomalies
- Robust incident response mechanisms
History of Zero Trust Concept
The Zero Trust concept originated in 2004 with the Jericho Forum’s de-perimeterization, focusing on network security. In 2014, Google’s BeyondCorp emphasized identity-based access without VPNs. In 2017, Gartner introduced CARTA (Continuous Adaptive Risk and Trust Assessment), promoting adaptive trust decisions. In 2018, Forrester expanded the model in its Zero Trust Extended Ecosystem Report, broadening Zero Trust beyond networks to include multiple security pillars.
Recently, NIST released in 2020 the Special Publication 800-207, and they talked about Zero Trust. They defined Zero Trust as a term for an evolving set of cybersecurity moves — a shift from static, network-based perimeter focus — to focus on users, assets, and resources.
Components of Zero Trust Architecture
These components work together to enforce secure, policy-based access control across users, devices, and enterprise resources.
 Core Components
Core ComponentsPolicy Engine (PE)
The Policy Engine (PE) is responsible for the ultimate decision to grant access to a resource for a given subject. The PE uses enterprise policy as well as input from external sources (e.g., CDM systems, threat intelligence services) as input to a trust algorithm to grant, deny, or revoke access to the resource. The PE is paired with the Policy Administrator component. The Policy Engine makes and logs the decision (as approved or denied).
Note: subject refers to the entity requesting access to a resource
Policy Administrator (PA)
The Policy Administrator (PA) is responsible for establishing and/or shutting down the communication path between a subject and a resource (via commands to relevant PEPs). It generates any session-specific authentication and authentication token or credential used by a client to access an enterprise resource. The PA communicates with the PEP when creating the communication path. This communication is done via the control plane. If the session is authorized and the request authenticated, the PA configures the PEP to allow the session to start. If the session is denied (or a previous approval is countermanded), the PA signals to the PEP to shut down the connection.
Policy Enforcement Point (PEP)
The Policy Enforcement Point (PEP) is responsible for enabling, monitoring, and eventually terminating connections between a subject and an enterprise resource. The PEP communicates with the PA to forward requests and/or receive policy updates. This is a single logical component but may be broken into two different components, the client-side (e.g., agent on a laptop) and resource-side (e.g., gateway component in front of resource) or a single portal component that acts as a gatekeeper for communication paths.
Continuous Diagnostics and Mitigation (CDM) System
The CDM system gathers information about the enterprise asset’s current state and applies updates to configuration and software components. It provides the Policy Engine with the information about the asset making an access request, such as:
- Whether it is running the appropriate patched OS
- Integrity of enterprise-approved software components
- Presence of non-approved components
- Known vulnerabilities
Threat Intelligence Feeds
Threat intelligence feed(s) provide information from internal or external sources that help the policy engine make access decisions. These feeds include:
- Data about newly discovered attacks or vulnerabilities
- Flaws in software
- Identified malware
- Reported attacks on assets
Identity Management System
The Identity Management System is responsible for:
- Creating, storing, and managing enterprise user accounts and identity records
- Includes subject information (e.g., name, email, certificates)
- Stores enterprise characteristics such as role, access attributes, and assigned assets
It often uses other systems (such as PKI) for associated artifacts and may include federated community links, supporting nonenterprise employees or collaboration with external partners.
Zero Trust Architecture Pillars
These five foundational pillars define the core areas that Zero Trust Architecture must secure across any organization.
.webp)
1. Identity
Identity refers to the attributes that describe both human and non-human users. In this controls are essential to manage each user’s access requests, ensuring that the appropriate access is granted without excessive rights. In this include
- Single Sign-On (SSO)
- Multi-Factor Authentication (MFA)
- Identity and Access Management (IAM) systems
2. Devices
A device refers to any asset that can connect to a network (e.g., servers, desktops and laptops, printers, mobile devices, IoT devices, and networking equipment), including bring-your-own-device (BYOD) assets.
3. Networks
A network refers to any communication channel, including internal networks, wireless, and the Internet. In this approaches include:
- Encrypting network traffic
- Microsegmentation instead of traditional segmentation
- Monitoring traffic to detect security issues and policy violations
4. Applications & Workloads
Applications and workloads refer to all systems, programs, and services operating on-premises, in the cloud, or on mobile devices. Applications cannot be trusted, and continuous monitoring at runtime is necessary to validate their behavior. Zero Trust architecture directs continuous monitoring and validation of these tools to ensure secure deployment and service delivery.
5. Data
Data encompasses all forms of information structured and unstructured, metadata, and fragments—stored or processed across systems, devices, applications, and networks. All data must be protected from unauthorized access and exfiltration, whether it is in motion, in use, or at rest.
Trust Algorithm in Zero Trust Architecture
Imagine an enterprise using a Zero Trust Architecture (ZTA) to keep its systems secure. In this setup, the Policy Engine (PE) acts like the brain, making critical decisions about who gets access to what. The Trust Algorithm (TA) is like the brain’s main thought process—it’s the step-by-step method the Policy Engine uses to decide whether to allow or block access to a resource, like a file, app, or network.
 Trust Algorithm
Trust AlgorithmThe PE takes input from multiple sources:
- Access request: This is the actual request from the subject. The resource requested is the primary information used, but information about the requester is also used (e.g., OS version, patch level).
- Subject database: This is the “who” that is requesting access. This includes human and process subjects, their attributes/privileges, and historical behavior patterns. Attributes of identity may include time and geolocation.
- Asset database and observable status: This contains the known state of enterprise-owned (and possibly known nonenterprise/BYOD) assets. This includes OS version, software presence and integrity, location, and patch level.
- Resource requirements: Policies that define the minimal requirements for access to the resource, such as authenticator assurance levels, network location, and data sensitivity.
- Threat intelligence: This includes attack signatures, communication patterns, newly discovered malware, and external/internal threat feeds.
Implementation Phases
Implementing Zero Trust Architecture is an incremental and strategic process. The approach involves rethinking access, trust, and workflows based on Zero Trust principles.
Step 1. Visualize
Identify all resources and their access points, and map out potential risks. Enterprises must start by discovering and categorizing data, applications, devices, identities, and services. Understand where these exist, who accesses them, and how they are accessed.
Step 2. Mitigate
Detect and stop threats, or at least minimize their impact when they occur. This includes defining policies and controls, establishing authentication methods such as risk-based MFA, and applying segmentation to prevent lateral movement. Protect against misuse of credentials and monitor endpoints and sessions continuously.
Step 3. Optimize
Expand protection across the entire IT infrastructure while optimizing the user experience. Apply Zero Trust across multi-cloud environments, legacy systems, SaaS platforms, unmanaged devices, and partner connections. Ensure continuous monitoring, policy refinement, and minimal disruption to authorized workflows.
Traditional Architectures vs Zero Trust Architecture (ZTA)
How security models differ in trust, access, enforcement, and adaptability across IT environments.
| Traditional Architectures | Zero Trust Architecture (ZTA) |
|---|
| Trust granted implicitly inside network perimeter | No implicit trust; trust is never assumed |
| Perimeter-based: Firewalls, VPNs, “castle-and-moat” model | No clear perimeter; protects resources anywhere |
| Broad access after login | Per-session dynamic access with least privilege |
| Devices/users inside perimeter considered safe | Every request treated as untrusted by default |
| Authentication only during login | Continuous authentication & authorization |
| Limited visibility; encrypted traffic hard to inspect | Full visibility with continuous diagnostics & monitoring |
| Lateral movement possible once inside | Prevents lateral movement via micro-segmentation |
| Hard to scale (centralized infrastructure) | Easily scales across cloud, hybrid, and mobile environments |
Benefits of Zero Trust Architecture
By implementing zero trust architecture, any organization can benefit in the following ways:
- Enhanced Security: Enforces least-privilege access, reducing attack surfaces and continuous authentication prevents unauthorized access, minimizing insider and outsider threats.
- Protection Against Data Breaches: Authentication for every request reduces breach risk, Assumes breach and limits lateral movement within the network.
- Improved Visibility and Monitoring: Continuous monitoring and logging improve threat detection, Better audit trails for more effective responses.
- Reduced Risk of Advanced Persistent Threats (APTs): Isolates network segments and verifies access at each level, minimizing the impact of APTs.
- Scalability: Easily scales with the growing number of users, devices, and applications.
- Improved Incident Response: Granular control helps security teams quickly identify and isolate compromised resources.
- Support for Remote Work and Cloud Environments: Secures distributed work forces and multi-cloud environments.
- Addresses Compliance Requirements: Aligns with regulations like GDPR, HIPAA, and PCI-DSS.
- Reduces Insider Threats: Limits access to necessary resources, preventing lateral movement and exposure.
Conclusion
Zero Trust Architecture is an approach, prioritizing the verification of every user, device, and application, regardless of their location. The core principle of "Never Trust, Always Verify" enhances an organization's ability to protect sensitive data and resources from both internal and external threats. By continually authenticating and segmenting access, Zero Trust ensures that unauthorized access is minimized, and potential breaches are contained.
Zero Trust integrates several key components, such as user and device security, application and data protection, and infrastructure security. Through a structured approach that includes authentication, encryption, least privilege access, and continuous monitoring, organizations can significantly reduce their vulnerability to cyberattacks.
Moreover, Zero Trust offers numerous benefits, including enhanced security, better visibility, protection against data breaches, and scalable solutions for both cloud environments and remote workforces. It also supports compliance with various data protection regulations and strengthens incident response capabilities.
Explore
Introduction to Ethical Hacking
Foot Printing and Reconnaissance
Scanning Networks
Enumeration
System Hacking
Malware Analysis
Sniffing
Social Engineering
Denial-of-Service
Session Hijacking