Applying Security Algorithms Using openSSL crypto library
- 1. Applying security algorithms using openssl crypto library B.C. Sekar HCL Technologies Limited NETWORKING PRODUCTS DIVISION, HCL
- 2. Agenda * Introduction * Overview of related security concepts. * Types of security algorithms * Overview of openssl crypto library * Using the security algorithms * Programming using crypto library. * Conclusion
- 3. Introduction * Security Algorithms form the basis of many security systems like SSH, HTTPS etc., * Growing use of web applications for e-commerce, banking and other security sensitive apps. * There is a clear need for securing communication. * Applying security algorithms is essential - if you are building or enhancing your security system
- 4. Agenda * Introduction * Overview of related security concepts . * Types of security algorithms * Overview of openssl crypto library * Using the security algorithms * Programming using crypto library. * Conclusion
- 5. Block Ciphers * Messages are broken down into blocks * Each of these are then encrypted M1 M2 M3 M4 Mn Plain Message (M) E E E E E C1 C2 C3 C4 Cn Cipher Message (C)
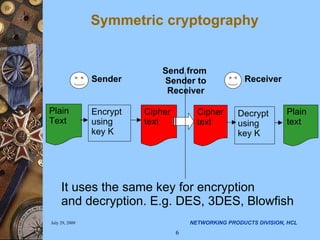
- 6. Symmetric cryptography It uses the same key for encryption and decryption. E.g. DES, 3DES, Blowfish Encrypt using key K Cipher text Sender Decrypt using key K Cipher text Plain text Receiver Send from Sender to Receiver Plain Text
- 7. Public key cryptography Public key is distributed whereas private key is kept secret. E.g. RSA, DSA Encrypt using B’s public key Cipher text A Decrypt using B’s private key Cipher text Plain text B Send from Sender to Receiver Plain Text
- 8. Hashing Function Hash Function Message digest Message Eg. a word “Linux conference” becomes EFDD2356. Typical Hash functions have an infinite domain, such as byte streams of arbitrary length and a finite range such as bit sequences of some fixed length.
- 9. Digital Signatures Hash Function Message digest Encrypt using Sender’s private key Digital Signature Message The message digest which is the hash value is Encrypted and anybody can check the signature using the public key.
- 10. The purpose of a Message authentication code is to authenticate a source of a message and and its integrity. MAC Hash Function Message digest Encrypt using symmetric key MAC Message
- 11. NETWORKING PRODUCTS DIVISION, HCL Digital Certificates Country Name: State: Locality: Organizational Name: Common Name: E-mail address: Public key Certificate Sign using private key of Self or trusted Certification Authority(CA).
- 12. Agenda * Introduction * Overview of related security concepts. * Types of security algorithms * Overview of openssl crypto library * Using the security algorithms * Programming using the crypto library. * Conclusion
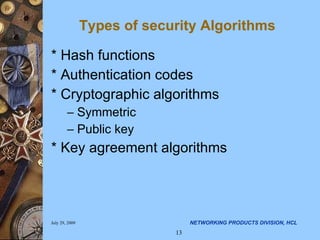
- 13. Types of security Algorithms * Hash functions * Authentication codes * Cryptographic algorithms Symmetric Public key * Key agreement algorithms
- 14. Hash functions – SHA-1 * SHA-1 Secure Hash Function-1 * Its Secure They are one way and collision free. * SHA-1 produces a 160-bit hash. * Because the number of possible hashes are so large, the probability of getting the same hash for a different message is smaller 2 80 by brute force. * Some cryptanalysts were able to do it in 2 69 .
- 15. Authentication codes - HMAC * Keyed-Hash Message Authentication code is used by the sender to produce a value that is formed by condensing the secret key and the message input. * A hash function such as SHA-1 will be used. * HMAC depends on the size and quality of key and size and quality of hash output length in bits. * HMAC-SHA-1 and HMAC-MD5 are used with IPSec and TLS protocols.
- 16. * It’s a block encryption algorithm is * Fast 26 clock cycles per byte in 32-bit microprocessors * Simple it uses XOR, addition * Secure its key length is variable and can be as long as 448 bits Cryptographic Algorithms – Symmetric - Blowfish
- 17. Cryptographic Algorithms – Public key * Unlike private key cryptography there is no need to share keys. Instead a public key is available to any user and a private key is held as secret. * Public key cryptography is based on the idea of a trapdoor function. * f: X Y * f is one to one, f is public, f -1 is difficult to compute, f is easy to compute and f -1 is easy to compute if a trapdoor is known.
- 18. Public key cryptography - RSA * Rivest Shamir Adleman * Find P and Q, two large prime numbers, N=PQ * Choose E such that E and (P-1)(Q-1) are relatively prime, which means they have no common factors except 1 * Find another number such that ED-1 is divisible by (P-1)(Q-1). * The values E and D are called public and private components respectively.
- 19. Public key cryptography – RSA …contd * The public key is the pair (E,N) and private key is the pair (D,N). * It is currently difficult to obtain D from (E,N).
- 20. Public key cryptography – RSA …contd * Encryption * Suppose Alice wants to send a message m to Bob. * Alice creates the cipher text c by exponentiation: c = m^e mod n, where e and n are Bob's public key. She sends c to Bob. To decrypt, Bob also exponentiates: m = c^d mod n; the relationship between e and d ensures that Bob correctly recovers m. Since only Bob knows d, only Bob can decrypt this message.
- 21. * Message Digest is computed. * Alice creates a digital signature s by exponentiation: s = m^d mod n , where d and n are Alice's private key. She sends m and s to Bob. To verify the signature, Bob exponentiates and checks that the message digest m is recovered: m = s^e mod n , where e and n are Alice's public key. Public key cryptography – RSA …contd
- 22. * The obvious way to do this attack is to factor the public modulus, n, into its two prime factors, p and q. From p, q, and e, the public exponent, the attacker can easily get d, the private exponent. * The hard part is factoring n; the security of RSA depends on factoring being difficult. In fact, the task of recovering the private key is equivalent to the task of factoring the modulus: you can use d to factor n, as well as use the factorization of n to find d RSA – How safe?
- 23. * The protocol allows two users to exchange a secret key without the aid of another secret key in an insecure medium * The protocol has two public system variables p and g. p is a prime number. g which is less than p, n = g^k mod p Key agreement algorithms – Diffie Hellman
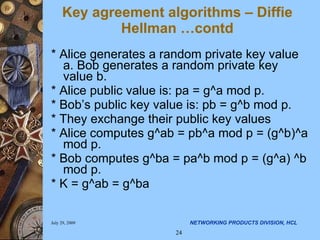
- 24. * Alice generates a random private key value a. Bob generates a random private key value b. * Alice public value is: pa = g^a mod p. * Bob’s public key value is: pb = g^b mod p. * They exchange their public key values * Alice computes g^ab = pb^a mod p = (g^b)^a mod p. * Bob computes g^ba = pa^b mod p = (g^a) ^b mod p. * K = g^ab = g^ba Key agreement algorithms – Diffie Hellman …contd
- 25. * It assumes that the given two public values g^a mod p and g^b mod p, its not feasible to calculate the shared secret key k = g^ab mod p. * There is Man in the middle attack vulnerability * The communicating parties are required to authenticate themselves by use of digital signatures and public key certificates. Key agreement algorithms – Diffie Hellman …contd
- 26. Agenda * Introduction * Overview of related security concepts. * Types of security algorithms * Overview of openssl crypto library * Using the security algorithms * Programming using crypto library * Conclusion
- 27. * The crypto library implements a wide variety of security algorithms. * Its used for implementation of SSL, TLS, SSH and OpenPGP and other standards. * Crypto library consists of many sub-libraries which implement the individual algorithms. OpenSSL crypto library
- 28. Crypto sub-libraries Sub-libraries Blowfish DES DH HMAC RSA SHA-1
- 29. OpenSSL CLIs * openssl is a CLI which has options to invoke the crypto subsystems and do the necessary security functionality. $ openssl list-cipher-commands base64 bf bf-cbc cast des
- 30. OpenSSL CLIs …contd $ openssl list-message-digest-commands md2 md4 md5 mdc2 rmd160 sha sha1
- 31. Agenda * Introduction * Overview of related security concepts. * Types of security algorithms * Overview of openssl crypto library * Using the security algorithms * Programming using crypto library. * Conclusion
- 32. Generating Authentication codes $ openssl dgst –sha1 args.c SHA1(args.c)= 7ee67eeb39f1ed1117855ca1986416d8052c9dcf $ openssl dgst -md5 args.c MD5(args.c)= 0e474915f4a0fb8af12594d11c2cf048
- 33. Using blowfish for file encryption/decryption $ openssl enc -bf -in test.txt -out test.enc enter bf-cbc encryption password: Verifying password - enter bf-cbc encryption password: $ openssl enc -d -bf -in test.enc -out test.txt enter bf-cbc decryption password:
- 34. Generate RSA keys Generating $ openssl genpkey -algorithm RSA -out key.pem Generating with protection $ openssl genpkey -algorithm RSA -out key.pem -bf -pass pass:hello The public key info is contained within the private key, so no separate public key is generated. Mainly used in web server cases.
- 35. Generate Diffie Hellman key * Generate 1024 bit DH parameters: openssl genpkey -genparam -algorithm DH -out dhp.pem -pkeyopt dh_paramgen_prime_len:1024 * Generate DH key from parameters: openssl genpkey -paramfile dhp.pem -out dhkey.pem
- 36. Agenda * Introduction * Overview of related security concepts. * Types of security Algorithms * Overview of openssl crypto library * Using the security Algorithms * Programming using crypto library. * Conclusion
- 37. Programming using Crypto library – Blowfish – Create a key * Step 1: Open /dev/random generate_symmetric_key() { if ((fd = open ( "/dev/random", O_RDONLY)) == -1) perror ("open error");
- 38. Programming using Crypto library – Blowfish – Create a key Step 2: Initialize key Read 16 bytes from /dev/random That gives 128-bit random symmetric key. Read 8 bytes to populate initialization vector. int bf_key[16]; int bf_vector[8]; if ((read (fd, bf_key, 16)) == -1) perror (“Could not read the key"); if ((read (fd, init_vector, 8)) == -1) perror ("read iv error");
- 39. Programming using Crypto library – Blowfish - Encrypt * Step 1: Create a cipher context EVP_CIPHER_CTX ctxt; EVP_CIPHER_CTX_init (&ctxt); * Step 2: Initialize encryption algorithm and key. EVP_EncryptInit ( &ctxt, EVP_bf_cbc (), bf_key, bf_vector); * Step 3: Read data in 1K size if ((n = read (infd, inbuff, 1024) == -1)
- 40. Programming using Crypto library – Blowfish - Encrypt * Step 4: Encrypt blocks of 1K size if (EVP_EncryptUpdate (&ctx, outbuf, &olen, inbuff, n) != 1) * Step 5: if (EVP_EncryptFinal (&ctx, outbuf + olen, &tlen) != 1) * Step 6: Write your encrypted buffer into a file. * Step 7: Cleanup context. EVP_CIPHER_CTX_cleanup (&ctx);
- 41. Programming using Crypto library – Blowfish - Decrypt * Likewise, use EVP_DecryptUpdate and EVP_DecryptFinal for decryption…
- 42. SSL/TLS Architecture Packet processing in SSL/TLS record protocol layer. Source: www.modssl.org
- 43. SSL/TLS connection establishment SSL/TLS Connection establishment. Source: www.modssl.org
- 44. Summary * We dealt with various security algorithms and how openssl CLI and crypto library provides a mechanism to apply those algorithms.
- 45. References http://www.openssl.org http://www.rsasecurity.com http://linuxgazette.net/issue87/vinayak.html
- 46. Questions B.C. Sekar HCL Technologies Limited, 49-50, Nelson Manikkam Road, Chennai - 600026. Phone - +91-44-23750171 [email_address] http://www.hcltech.com



































![Programming using Crypto library – Blowfish – Create a key Step 2: Initialize key Read 16 bytes from /dev/random That gives 128-bit random symmetric key. Read 8 bytes to populate initialization vector. int bf_key[16]; int bf_vector[8]; if ((read (fd, bf_key, 16)) == -1) perror (“Could not read the key"); if ((read (fd, init_vector, 8)) == -1) perror ("read iv error");](https://image.slidesharecdn.com/applying-security-algorithms-using-openssl-crypto-library-4634/85/Applying-Security-Algorithms-Using-openSSL-crypto-library-38-320.jpg)







![Questions B.C. Sekar HCL Technologies Limited, 49-50, Nelson Manikkam Road, Chennai - 600026. Phone - +91-44-23750171 [email_address] http://www.hcltech.com](https://image.slidesharecdn.com/applying-security-algorithms-using-openssl-crypto-library-4634/85/Applying-Security-Algorithms-Using-openSSL-crypto-library-46-320.jpg)