Esage on non-existent 0-days, stable binary exploits and user interaction
- 1. On non-existent 0-days, stable binary exploits and user interaction Alisa Esage Esage Lab // ООО ЦОР
- 2. GOAL NEED SOME 0-DAY REMOTE EXPLOITS* FOR TOP SOFTWARE/OS, FAST
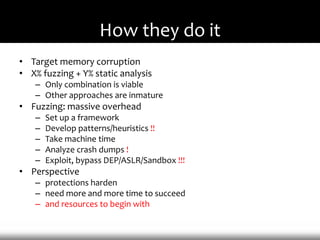
- 3. How they do it • Target memory corruption • X% fuzzing + Y% static analysis – Only combination is viable – Other approaches are inmature • Fuzzing: massive overhead – Set up a framework – Develop patterns/heuristics !! – Take machine time – Analyze crash dumps ! – Exploit, bypass DEP/ASLR/Sandbox !!! • Perspective – protections harden – need more and more time to succeed – and resources to begin with
- 4. Perspective vectors • By-design vulnerabilities – E.g. DLL Hijacking, UI redressing, LD_LIBRARY_PATH… • Sandbox bypass for complex systems – E.g. JAVA: bypass SecurityManager -> full privileges for unsigned applet -> win • Certificates – E.g. Adobe PDF: signed document -> trusted document -> full-privileged JavaScript -> win
- 5. Why DLL Hijacking? • Test hacking skills! – Succeed with a blind alley before hitting the highway • Looks easy – Plenty of previous research, e.g. binaryplanting.com – Interns must do research, too • Real world targetted attacks: CVE-2011-1980, CVE-2011- 1991, CVE-2011-2100 – They work • MS12-046 vbe6.dll – They still exist! • OS behaviour undocumented – There is place for research
- 6. Research focus • Top, clean platforms – Windows 7 – Windows XP – Office 2010 – Office 2007 – Adobe Acrobat/Reader • Find a new remote delivery vector – Not a “.dll” in e-mail attachment – Not a “.dll” in a network share • Find something yet unfound
- 7. Tech recap • Exe -> dll by relative path • DLL Search Order • Current Directory (CD) – MS DOS rudiment • Default: app path • File open: file path • Some other changes • Exploitation profit: Bypass restrictions, LPE, RCE • Vectors: local, local network, client-side
- 8. Advantages • 100% stable exploit • 100% silent execution on non-supported targets • Very little overhead • No mess with protections • ! Not fixable globally with simple measures like DEP/ASLR – Only developers education can help – Will reappear in new software forever
- 9. Challenges • Search – “Trivial => already found” myth • Exploitation – Nobody ever tried to manipulate CD • User interaction – Triggered by clicking menus… now what? • Masking / delivery – Document + DLL binding looks suspicious
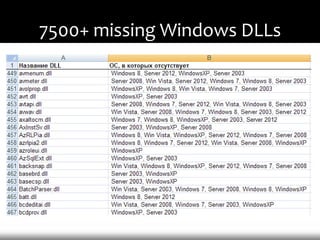
- 11. 7500+ missing Windows DLLs
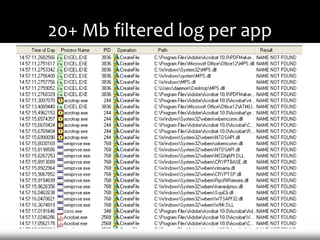
- 12. 20+ Mb filtered log per app
- 14. Good!
- 15. Not so good
- 17. CD internals • 0:005> dt _PEB @$peb -r • ntdll!_PEB • ... • +0x010 ProcessParameters : 0x00020000 _RTL_USER_PROCESS_PARAMETERS • ... • +0x024 CurrentDirectory : _CURDIR • +0x000 DosPath : _UNICODE_STRING "C:Documents and SettingshMy Documents" • +0x008 Handle : 0x00000b50 Void • • // получение адреса CurrentDirectory (первый dword - размеры, второй – указатель на строку) • 0:005> dd poi(@$peb+0x010)+0x024 • 00020024 02080052 00020290 00000b50 01840182 • 00020034 00020498 006e006c 0002061c 00740072 • // проверка адреса CD • 0:005> du 0x20290 • 00020290 "C:Documents and SettingshMy D" • 000202d0 "ocuments" • • // точка останова • 0:005> ba w 4 0x20290
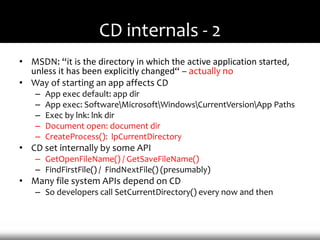
- 18. CD internals - 2 • MSDN: “it is the directory in which the active application started, unless it has been explicitly changed“ – actually no • Way of starting an app affects CD – App exec default: app dir – App exec: SoftwareMicrosoftWindowsCurrentVersionApp Paths – Exec by lnk: lnk dir – Document open: document dir – CreateProcess(): lpCurrentDirectory • CD set internally by some API – GetOpenFileName() / GetSaveFileName() – FindFirstFile() / FindNextFile() (presumably) • Many file system APIs depend on CD – So developers call SetCurrentDirectory() every now and then
- 19. So…?
- 20. Local exploitation • Bypass restrictions/LPE: place exploit DLL into unrestricted location • Consider %PATH%
- 21. PATH FTW
- 22. Remote exploitation • Just open a document (the lucky case) • Make user Open/Save/Import/Export files, then trigger • Or automate file operations with a script • Induce an app state with CD changed by developer • Set CD explicitly • Find an app that CreateProcess()-es vulnerable app with good CD
- 23. Arguing myths EXPLOIT DLL TOO OBVIOUS?
- 24. No hiding
- 25. A needle in the haystack
- 26. Torrents
- 27. Browser UI redressing • IE9 on Windows 7 • Context: Local directory, network shared directory, WebDAV • Explorer dir underneath a website • Demo • Also works in Chrome on Windows 7, but restricted to file download operations
- 28. Browser UI redressing (2) • Chrome on Windows 7 • Context: remote • Web server directory underneath a website • Click-jacking game to silently download necessary files one-by-one • Until all files are saved in %Downloads% • Open exploit document
- 29. Set CD macro (MS Office) • Context: local dir, network shared dir • You can just execute arbitrary DLL from a macro • But better to execute a kernel32!SetCurrentDirectory() API to fool forensic analysts • Demo
- 30. MHT • Single file in e-mail attachment • Can contain any types of files, incl. binary • Browser extracts files to %INET_TMP% • Open exploit document by clicking <a href=“.filesdocument.txt” • Exploit DLL will be executed from the same directory • IE9 on Windows 7
- 31. Archives • Any archives for Windows that extract all files by default? Not SFX of course • WinRAR (latest): browse archive, double- click a HTML document only – Will extract ALL files into %TMP% – Including exploit DLL – Local browser context already
- 32. WinRAR FTW
- 33. Multistage • Case: DLL triggered by manual file import, no registered extension handler – unexploitable? • Stage 1: User gets an e-mail from admin (fake) instructing to install the attached reg-file (looks innocent) • In two weeks, stage 2: user gets an e-mail from a friend with a RAR-ed html game • Click-jacked open file -> exploit • Or open file via network share • As simple as the user is
- 34. So, what do we have? • Some 0-day vulnerabilities in up-to-date top platforms – Think of non-top software • Ways to manipulate CD • Ways to hide DLL • Remote DLL Hijacking exploitation looks like normal client-side exploitation • What else?
- 35. Conclusions • Is this a good vector for mass attacks? – Authors of CVE-2011-1991, 1980, 2100 could tell us for sure – I say no – 0-day exploits are not necessary for mass attacks anyway • Excellent vector for rapid targeted/onsite attacks – Plenty of vulnerabilities everywhere – Easy ‘n fast to find in arbitrary environment – Ease ‘n fast to exploit (after this presentation ) • Even the most trivial bug can be worked down to a good exploit
- 36. Questions? Thanks to my team and interns Thank you for attention @alisaesage