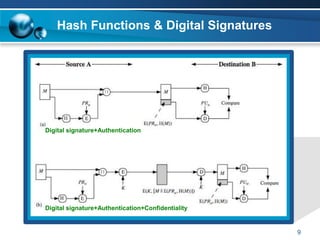
This document discusses hash functions and their cryptographic applications. It begins by defining hash functions and their properties like one-wayness and collision resistance. It then discusses various applications of cryptographic hash functions like message authentication codes, digital signatures, password files, and more. It provides details on how hash functions are used for message authentication and digital signatures. It also describes the Secure Hash Algorithm family of hash functions like SHA-1, SHA-2, and the NIST competition for the SHA-3 standard.